Episode 187
Posted on Friday, Feb 17, 2023
Show Notes
Overview
After the announcement of Ubuntu Pro GA last week, we take the time to dispel some myths around all things Ubuntu Pro, esm-apps and apt etc, plus Camila sits down with Mark and David to discuss the backstory of Editorconfig CVE-2023-0341 and we also have a brief summary of the security updates from the past week.
Ubuntu Pro, esm-apps and apt confusions [00:40]
-
https://www.theregister.com/2022/10/13/canonical_ubuntu_ad/
- talks in general about Ubuntu Pro notices in apt but doesn’t cover any details
-
https://www.omgubuntu.co.uk/2022/10/ubuntu-pro-terminal-ad
- talks more about the details but seems to think it is only beneficial for LTS releasing at the end of the LTS
-
https://news.ycombinator.com/item?id=33260896
- almost no engagement on hacker news
-
But there has been a lot of users expressing a lot of emotion over the appearance now of the new ‘advertisement’ for Ubuntu Pro / esm-apps when they run apt update, e.g.:
The following security updates require Ubuntu Pro with 'esm-apps' enabled: python2.7-minimal python2.7 libpython2.7-minimal libpython2.7-stdlib Learn more about Ubuntu Pro at https://ubuntu.com/pro -
There appears to be a few main issues:
- Users don’t like what appears to be an advertisement in the apt output
- Some updates now appear to be behind a “paywall”
- Whilst they are free for personal use, to get access to them you need to register an account on Ubuntu One etc and this requires providing various high-level personal details (Name, Email etc)
-
So let’s take some time to look into these issues:
- This is not the first time Canonical has tried to raise awareness of
various products - e.g. motd etc - so perhaps this causes more frustration
for users - however, if desired it can be disabled:
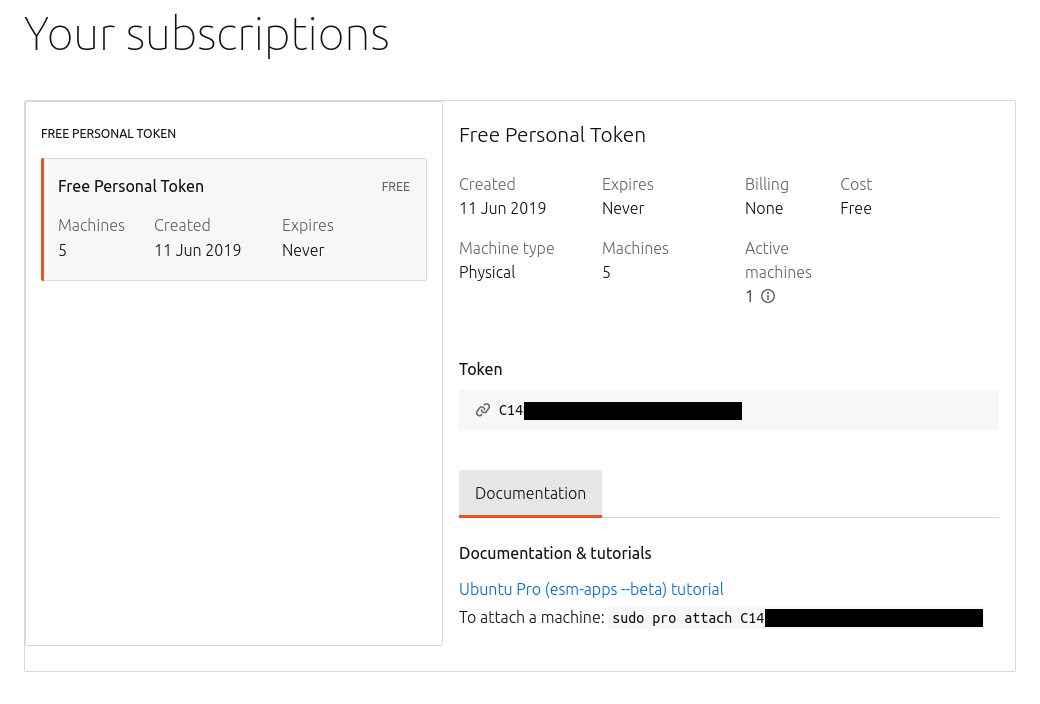
pro config set apt_news False - Ubuntu Pro is free for personal / small-scale commercial use - any user is
entitled to a free Ubuntu Pro subscription on up to 5 machines
- this can be for bare metal or virtual machines and using either Ubuntu Server or Desktop - the install / Ubuntu type doesn’t matter
- and as we mentioned last week, if you are an Ubuntu member you get an
entitlement for 50 machines
- currently this is not reflected in the https://ubuntu.com/pro/dashboard (it still says 5 machines against the free personal token)
- This is not the first time Canonical has tried to raise awareness of
various products - e.g. motd etc - so perhaps this causes more frustration
for users - however, if desired it can be disabled:
- so there is nothing to pay here - likely most folks that find this objectionable are personal users and so are entitled to the free subscription
- the other big part of this is that some folks seem to think these updates
are now only available via Ubuntu Pro when previously they were part of
the regular Ubuntu archive
- this is incorrect - the
esm-appspart of this message indicates that these updates are for packages in the Universe component of the Ubuntu archive - previously this has only ever been community supported - and so the Ubuntu Security team would only ever provide security updates on rare occasions OR if a member of the community came along and provided an update in the form of a debdiff which could be sponsored by someone from the Ubuntu Security team - but now the team is starting to do security updates for packages in Universe and these are being made available via Ubuntu Pro
- so if you do not enrol in Ubuntu Pro, your machine is still getting the regular security updates for the Main+Restricted components as it always was
- but if you do choose to enrol in Ubuntu Pro you can get these extra security updates that were never previously available
- this is incorrect - the
- On the issue of having to provide some personal information to get access to Ubuntu One, I realise this can be a bit contentious given that a lot of Ubuntu and Linux users in general can be quite privacy conscious - however this is not really any different than other online services like Github/Gmail etc - and as said earlier, if you choose to not enrol in Ubuntu Pro, you are just as secure as you always were - and to avoid having to see the prompt in your apt update output, you can disable that as mentioned earlier and so restore your system to the same state as it used to be - as always, you are in control of your own machine
- Hopefully this helps to dispel some of the myths and concerns surrounding Ubuntu Pro and encourage folks to use it - the Ubuntu Security Team and others at Canonical have put a lot of work into Ubuntu Pro behind the scenes and we think this provides a lot of great security benefits and so encourage all listeners to make use of it to ensure their systems are as secure as possible
The inside story of Editorconfig CVE-2023-0341 [09:05]
- Interview by Camila Camargo de Matos with David Fernandez Gonzalez and Mark Esler about the discovery and investigation of CVE-2023-0341 in Editorconfig ([USN-5842-1] EditorConfig Core C vulnerability from Episode 186)
- Keynote: Improving FOSS Security - Mark Esler | UbuCon Asia 2022
- https://litios.github.io/2023/01/14/CVE-2023-0341.html
This week in Ubuntu Security Updates [25:19]
64 unique CVEs addressed
[USN-5849-1] Heimdal vulnerabilities
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5835-4] Cinder vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5835-5] Nova vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-5852-1] OpenStack Swift vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5850-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Kinetic (22.10)
[USN-5854-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS)
[USN-5855-1] ImageMagick vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-5856-1] Linux kernel (OEM) vulnerabilities
- 3 CVEs addressed in Jammy (22.04 LTS)
[USN-5857-1] Linux kernel (OEM) vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
[USN-5858-1] Linux kernel (OEM) vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS)
[USN-5859-1] Linux kernel (OEM) vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-5848-1] less vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
[USN-5860-1] Linux kernel (GKE) vulnerabilities
- 14 CVEs addressed in Jammy (22.04 LTS)
[USN-5861-1] Linux kernel (Dell300x) vulnerabilities
- 15 CVEs addressed in Bionic (18.04 LTS)
[USN-5862-1] Linux kernel (Qualcomm Snapdragon) vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS)
[USN-5863-1] Linux kernel (Azure) vulnerabilities
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5865-1] Linux kernel (Azure) vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS)
[USN-5866-1] Nova vulnerabilities
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5867-1] WebKitGTK vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5864-1] Fig2dev vulnerabilities
- 14 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[LSN-0091-1] Linux kernel vulnerability
- 2 CVEs addressed in
[USN-5869-1] HAProxy vulnerability
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5871-1] Git vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5870-1] apr-util vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)